How to use the Task Manager
 Task Manager
Task Manager is a tool that allows you to easily monitor your computer's activity and which helps you control the programs, services and processes that are currently running. You can also view details about the network traffic, the performance of the computer and the number of users that are connected at a given time. In this article I will show you how to use this tool and I'll present you its most important features and options.
How to start the Task Manager
To open the Task Manager just right click somewhere on the empty space of the taskbar and click on Task Manager.

A more refined way is to press the keys CTRL + SHIFT + Esc or press CTRL + ALT + DEL and then click on the Task Manager link.

Another way is to open the Start Menu, type taskmgr or taskmgr.exe in the search box and press Enter.

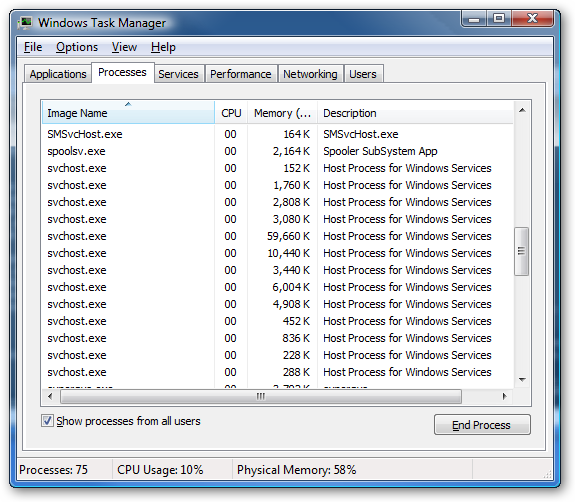
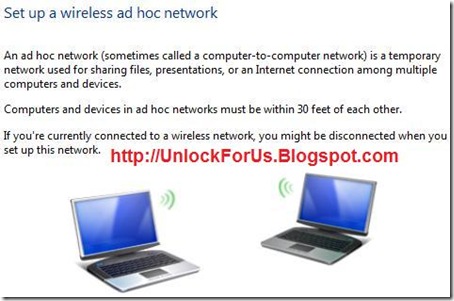
Once you open it, Task Manager should look like in the screenshot below.

As you can see, the Task Manager window has a series of menus and tabs with different options. First, we will show you what options are available in each tab and then we will present what can be done in each menu.
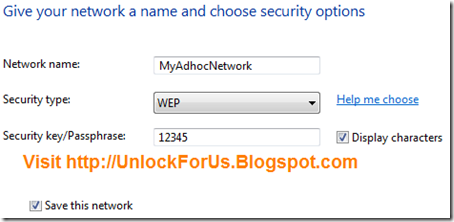
Possible Problem: if the Task Manager window has no menus and tabs, just like in the screenshot below, it means that it is running in the so called tiny footprint mode.

To have your Task Manager window return to normal, double click on the blank gray area which I highlighted above.
How to work with the Applications tab
In the Applications tab you can force an application to close if it is not working properly by selecting it and clicking on the End Task button. However, you should be careful when closing an application with the End Task option because you might lose important data that hasn't been saved. The End Task should be used only when an application is not responding. When that happens, Task Manager will show 'Not responding' in the Status column.

To see what process an application is using, just right click on the desired application and, in the context menu, click on 'Go To Process'. This will automatically send you to the Processes tab, where you will see the process associated to the selected application.

When you right click on an application you will see several options including 'Switch To' and 'Bring to front'. Choosing 'Switch To', will make that application be the active one instead of the current one and it will be brought to the front of your Desktop. Choosing 'Bring to front' will also bring the selected application to the front of your Desktop. However, it won't work if there is another program that has the property Always on top set.
The last important thing that can be found in the Applications tab is the New Task button. It can also be found in the top menu bar by clicking on the File menu. This is similar to the Run button in the Start Menu and you can use it to start other applications.
How to work with the Processes tab
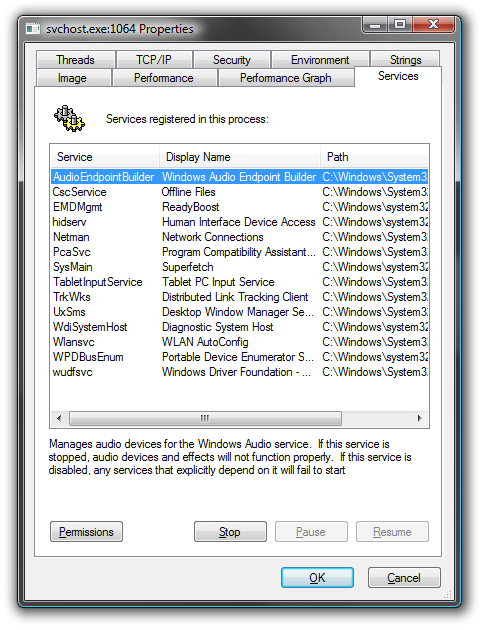
The Processes tab gives you information about the processes that are running on your PC. If you want to know more about a certain process, select it with the mouse, right click on it and select Properties.
If you want to know the exact location where a certain process can be found on the hard disk, select it with the mouse, right click on it and select Open File Location.

Task Manager will open a Windows Explorer window which shows the folder from where the process is running.
Sometimes a process can be the parent of other processes known as children processes. This hierarchy relation between processes is similar to a family tree. If you want to end a parent process and its children processes you should use the End Process Tree option. To end a process tree, right click on the process you want to end and, in the context menu, click on the End Process Tree. However, don't use this option without further analysis because you might also end a process that you still want to have running.

Another useful option in the Processes tab is the priority option. This option allows you to set which application will receive more attention from the operating system. The more attention a process receives, the faster that process is being listened by Windows Vista. However, if one process gets too much attention, the other ones will get less considered, so caution is needed. To change the priority of a process, right click on a process and go to 'Set Priority' and select one of the available options.

One of the most unused but powerful features that Windows Vista has is the 'Processor Affinity'. This is an useful option if you have, for example, a multi-core processor in your computer. If you do, you can make some processes run on one processor and the rest on the second, third, etc. This will, in some cases, make the computer work more efficiently. However, if you are to set affinity to the processes, try to split the work done by them. To use this option, right click on a process and click on 'Set Affinity...'. A new window will appear and you will have to decide, by checking one of the boxes, on which processor you want to run that process. If you are not sure you want to work with this, you should leave it as it is but you should know that the changes you have made will not be permanent. They will revert to default once the application is closed or when the computer is restarted.

If you want to have more information about the running processes, you can add more columns. Almost every tab has more columns that are available for you to use. To view other columns, click on the View menu and select 'Set Columns'. After you have selected the columns you wish to see, click OK and now you will have those column appear in the processes tab.

If you want to arrange columns in a specified order you just need to click, hold and drag the name of that tab to the desired place.

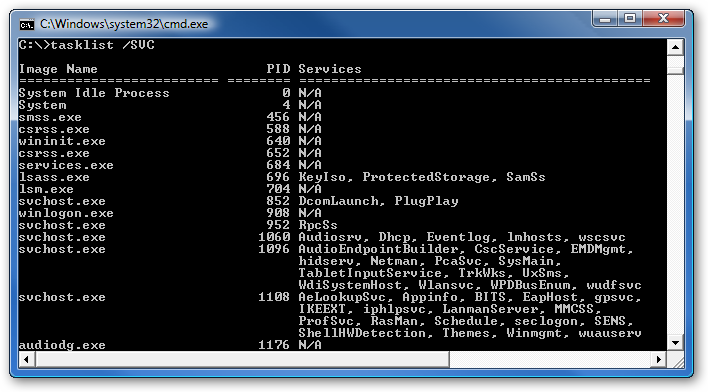
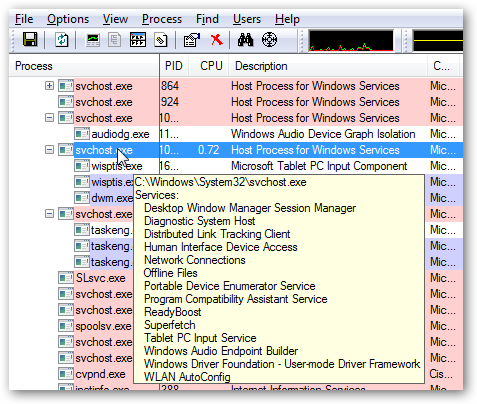
To see the service that is running behind a certain process right click on the process and click on 'Go to Service(s)'. If the process has a service running you will be automatically taken to it. If not, you will be shown the Services tab but nothing will be selected.
How to work with the Services tab
A service is an application or process that runs deep into the heart of the operating system. For example, you can find services related to the printer, the network, Windows Defender, Event Log and much more. However, while all services can be changed some are better left as they are by default. In the Services tab, right click on a service and click to Stop or Start the selected service.
For more details about the service(s) running you can click on the Services button.

How to work with the Performance tab
To see the performance of your computer click on the Performance tab. Here, you will see details regarding your computer. The Performance tab is self explanatory. It shows the performance of your computer with the help of graphs and numbers. Basically, the idea is to have the graph line to a low altitude and the numbers to an acceptable level. If the performance of the computer is problematic and slows your everyday activity you can study its cause with the help of these graphs and numbers. For a more in depth view of the performance you can click on the 'Resource Monitor' button.

How to work with the Networking tab
If you are connected to a network, you can monitor details about its connection in the Networking tab. For more details you can use the View menu, go to 'Select columns' and add more columns to thoroughly examine your network traffic. Another way to see details about your network connection is to open the 'Resource Monitor' from the Performance tab.

How to work with the Users tab
The Users tab shows who is currently connected to your computer. If you want to know the location of an user, connected on your computer or to the network, click on the Users tab and from the top menu and the on Options. In the menu that appears under the Options click on 'Show Full Account Name'. In the User column of the Users tab you will now see the full location path of that user.
Sometimes you might want to send a message to another user that is connected to the computer but is not around at the time. To do this, click on the Users tab and select the user to whom you wish to send your message. Once you have selected the user click on the 'Send message' button.

A new window will appear and in that window you can send your message. When the user logs in, he will receive your message.

However, if you have a limited account, meaning not an administrator, then you might have surprises when sending such messages. If this happens, you might consider other alternatives for sending messages.

Also, if you want to close somebody's connection to the computer, click on the Users tab, select the user and click on the Logoff button. Windows Vista will warn you about the decision you are about to take. If you are sure that you want to end the users session, click on the Log off user button.

Enable or Disable the Always On Top option
The Task Manager has the 'Always on top' option activated. This makes it show up in front of other applications. Even if you open a new application, or click on an application that is already opened, it will show up behind Task Manager. To disable this feature and make Task Manager act as a regular window, click on the Options menu and then on Always on top so that this option will be disabled.

How to quickly see the Task Manager if minimized
If you disabled the 'Always on top' or made the Task Manager to hide when minimized, you can quickly see it again by clicking on its icon from the taskbar.










 Task Manager is a tool that allows you to easily monitor your computer's activity and which helps you control the programs, services and processes that are currently running. You can also view details about the network traffic, the performance of the computer and the number of users that are connected at a given time. In this article I will show you how to use this tool and I'll present you its most important features and options.
Task Manager is a tool that allows you to easily monitor your computer's activity and which helps you control the programs, services and processes that are currently running. You can also view details about the network traffic, the performance of the computer and the number of users that are connected at a given time. In this article I will show you how to use this tool and I'll present you its most important features and options.